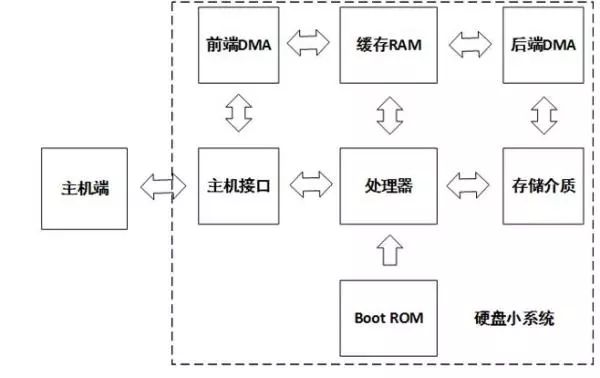
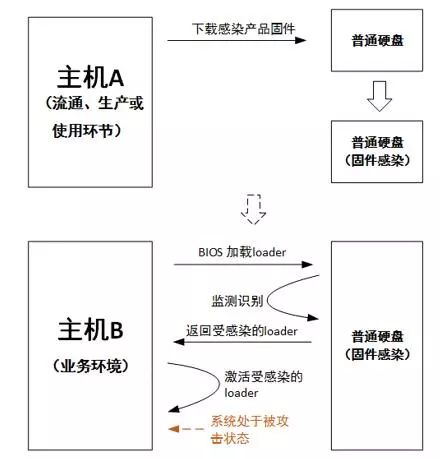
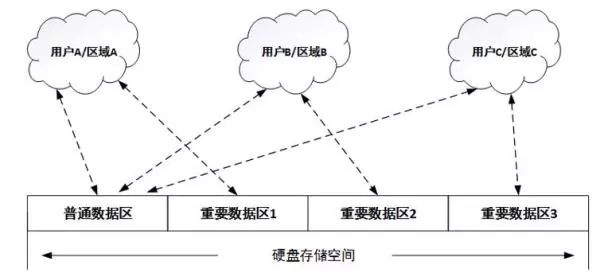
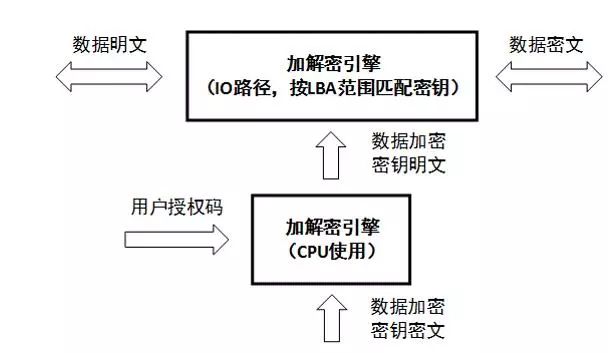
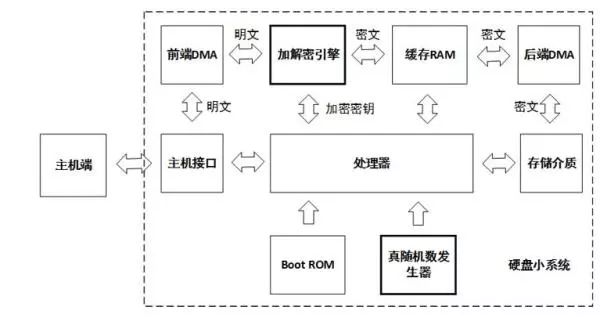
As individuals and businesses increasingly focus on data security, they often purchase a variety of security products, such as firewalls, VPNs, intrusion prevention systems, application control gateways, and various anti-virus software. They hope to construct a comprehensive security office application environment. All data is generated and applied in such a secure environment to ensure data security. Many times, the security of data is far greater than the value of the device itself. However, with such a set of security systems, is our data really safe? Data is inseparable from storage, as the final carrier hard disk for data storage, providing the final storage space for data. All data that needs to be permanently recorded must be stored on a permanent storage carrier such as a hard disk. The data is stored on the hard disk. Is the data read and written by the hard disk reliable? is it safe? Hard disk structure and principle The hard disk is currently mainly divided into mechanical hard disk and solid state hard disk (SSD). Let's take a look at the principle and structure of the hard disk, as shown in the following figure: This is a simplified hard disk structure diagram, and the mechanical hard disk and solid state drive SSD have a similar structure. As can be seen from the above figure, there is actually a small system inside the hard disk, which has a processor, a ROM, and a cache RAM. The processor runs firmware, is responsible for initializing peripheral modules, drives peripheral modules to complete command and data processing, and transmission control; the cache is used for data transfer between the host and the storage medium; the host interface is responsible for docking the host side commands. Protocol and data transfer; ROM is responsible for loading the product firmware that the processor provides for storage services. For mechanical hard drives, the product firmware may be stored on the EEPROM of a separate I2C interface or on the NOR Flash of the SPI interface. For SSDs, the firmware of the product is usually stored in the system area on the NAND Flash (defined by firmware, user Invisible area). The product firmware may be written by the hard disk manufacturer at the factory, or it may be in the subsequent use process, or an intermediate link is upgraded and written by the upgrade tool. Almost all hard disk manufacturers, offering factors such as fixing software bugs, will provide upgrades. When the hard disk is powered on, the processor executes the Boot ROM, the Boot ROM reloads the product firmware, and then transfers the CPU control to the product firmware. After the product firmware obtains control rights, the host service accesses the data by controlling the host interface, DMA, and cache resources. Since the product firmware is stored in the system area of ​​the hard disk and runs on the internal small system of the hard disk, this part of the data and processing is independent of the security system of the host and is not monitored by any security measures. Therefore, how the data is handled is completely controlled by the product firmware itself, and the reliability and security of the product firmware itself largely determine the reliability and security of the data. So, the question is, is our product firmware safe? If it is not safe, how to ensure safety? Firmware and security When the hard disk manufacturer releases the firmware, some manufacturers simply write some of the manufacturer's logo and version identifier in the firmware header to simplify the processing, which is convenient for identification in subsequent production and upgrade scenarios; some do more, in front. Based on the firmware, a CRC check is performed to check the integrity of the firmware data. The former can identify whether it is its own firmware and the corresponding version number, the latter can further see whether the firmware has changed during the transmission. These methods can meet the needs of most applications, but can not prevent special users with malicious purposes to make targeted modifications (hacker behavior), inject malware code, and then recalculate the new CRC to disguise Legal firmware. This camouflaged firmware can be written in an upgrade mode at all points of the hard disk circulation and use, and is stationed in the small internal system of the hard disk when it is reused, and is not found by any security measures at all. If this firmware with malicious code takes over the internal small system of the hard disk, then he can do more terrible things. For example, identifying and intercepting the BIOS read loader read command returns the infected loader data. If the bios loads the infected loader and gives the CPU control to the loader, then you can do more attacks, such as intercepting passwords. Moreover, the infected loader is very concealed (not in the visible area of ​​the hard disk user), and is activated during the system startup phase, and can be revived indefinitely, which is extremely harmful. The malicious firmware can also intercept and modify the content by detecting the read and write data content of the fixed feature or address; or recording the content, writing it to the invisible area of ​​the system, waiting for the appropriate time to obtain the recorded content and other illegal activities. This kind of direct attack on the hard disk firmware is highly concealed and difficult to find, but it is very harmful. It has been used by the famous "formula organization" and attacked hard disks of several hard disk manufacturers, including China, Russia, Britain, etc. More than 30 countries. In fact, this kind of attack is easy to prevent, because the illegal firmware must be downloaded to the internal hard disk and loaded by the internal ROM before it can run. Hard disk manufacturers can completely eliminate illegal firmware downloads and gain control of the CPU by checking the firmware for legality during production, upgrade, and ROM loading. If the firmware is signed when the version is released, the hard disk checks the downloaded firmware during production and upgrade, and the entire firmware is checked when the ROM is loaded. All operations guarantee that the firmware is truly legal, and in theory, all malicious acts of malicious purpose are eliminated. If the firmware is legally secure, is the data safe in all scenarios? Legitimate and secure firmware keeps the drive in a safe operating environment. However, when we usually use it, usually one environment is used by multiple people, or we need to move the hard disk frequently to access multiple different host environments. Is the data safe in such an application scenario? Data Security The data stored by the user on the hard disk may be of different importance to the user due to different content. How to ensure that users accessing specific data content must be genuinely corresponding legitimate users? You may first think that this can be guaranteed by the system, and has nothing to do with the hard disk. Then, plus one, if this hard drive is a mobile hard disk? In some special application scenarios, our mobile hard disk may be accessed in multiple different security environments. How to ensure that users who access data from a storage perspective are authorized users? If data access is bound to user rights one-to-one, when the user accesses a specific range of data, the corresponding interval authorization is required. After the hard disk is authenticated by the hard disk according to the interval range, the data access is allowed. , will undoubtedly meet the greatest possibility of data access security. Further, the data of different intervals is encrypted and stored using different keys, and the encryption key must be bound to the authorization code of the corresponding interval, and only the correct authorization code can unlock the encryption key of the corresponding data area. One way, the data will get the most security. Firmware security ensures that only legitimate firmware can be downloaded to the hard disk during production and upgrade. Data security ensures that only users with data access authorization can access important data in the corresponding area to ensure access legality. So, how does the data after the hard disk is eliminated to ensure that the data is not illegally accessed? Data destruction Hard disks may face upgrades or eliminations due to capacity, performance, reliability, etc. However, usually such a hard disk has a high probability of being re-circulated or illegally obtained by a malicious user, and such a hard disk may have important data and information that are easily overlooked by us. The general approach may be to format the entire hard drive, or to prevent such hard drives from re-circulating and unifying physical destruction. However, such a method is time consuming and does not necessarily delete the data on the hard disk; the latter can be destroyed, but the cost is increased. Is there a way to reduce the data on the hard disk quickly and theoretically unable to recover the data again after destruction? The answer is of course affirmative, and some hard disk manufacturers that have done a good job have already supported it. At present, the SSD hard disk solution of Guoke Micro has this function, which is the safe erasing of the hard disk. All hard drives that support Secure Erase are encrypted and stored in an industry or nationally recognized encryption algorithm. When data destruction is required, we only need to send a secure erase command to the hard disk. After the hard disk receives the command, the data encryption key is destroyed. Once the encryption key of the data is destroyed, the ciphertext data stored on the hard disk can no longer be recovered. Of course, the key used for data encryption must be unique to different hard disks, even unique to different areas of the same hard disk, and randomly generated. The storage method must also be stored in cipher text so that the key can be guaranteed. Uniqueness and non-replication. Once the key is destroyed, it is technically impossible to find the possibility of recovery. Only the real hard drive from the aspects of production, distribution, application and recycling, such as firmware security, data security, data destruction and other safe design, can be regarded as a true secure storage product. A security solution can be said to be a true security solution only if it is used in every node and link. It is a security solution that can be fully protected. 48V Battery Pack ,Switch Battery Pack,Portable Lithium Battery Pack,48V Lithium Ion Battery Pack Zhejiang Casnovo Materials Co., Ltd. , https://www.casnovo-new-energy.com
March 03, 2023